Additional Information
Other way to run Kali
Using Container
Using WSL
Test Your Linux Commands Knowledge
Command Explain
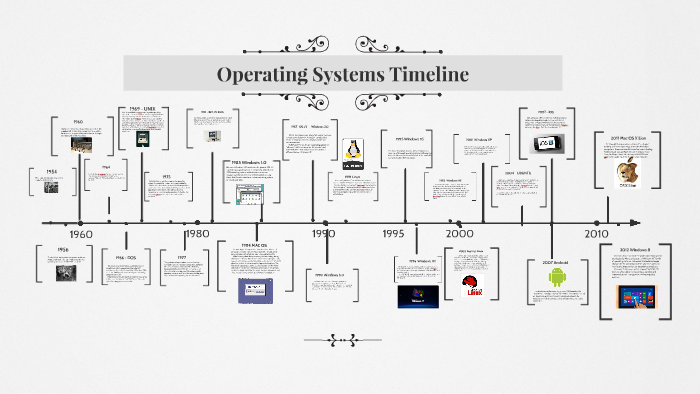
The History of OS
All Linux Distributions
Valuable Books
Linux Basics for Hackers
Other Linux Courses
Windows Command Lines (CMD Commands)
Last updated
